Tool Release: CB Bot
Today, I release CB Bot! CB Bot is a threat hunting and incident response web
It's been a while since I last wrote a blog post. I've been busy building cool stuff and hunting for evil, so now I'm back to writing blog posts. For a while, I have had folks ask me about RDP Bitmap Cache, so I decided to write one about it.

It's been a while since I last wrote a blog post. I've been busy building cool stuff and hunting for evil, so now I'm back to writing blog posts. For a while, I have had folks ask me about RDP Bitmap Cache and why I love it, so I decided to write one about it. It's definitely not new, but it's something that not a lot of people talk about it. And to be perfectly honest, it pretty much boils down to the question: is it even useful for forensics? Every time I try to answer this question, I always get divided opinions, and that's absolutely acceptable. But since I have had great success with this artifact in the past, I decided to write one up. So, let's all get nerdy about RDP Bitmap Cache 🤓 (WARNING: this is not the last emoji that you will see in this blog post).
I love forensics and being able to solve complex puzzles. However, when you deal with other folks that aren't really that technical, they would rather have you show them what happened, instead of trying to explain technical concepts such as: what is AppCompatCache or what is Mimikatz. I have found in a couple of investigations that this artifact is by far the best one to show folks exactly what the attacker was viewing. In fact, in some cases, I have been able to help clients determine that data has been exilfrated from their environment or even show that malware has been dumped on different domains and systems that we didn't have visibility into. Like they say, "a picture is worth a thousand words", and it really resonates to what RDP Bitmap Cache represents.
Remote Desktop Protocol (RDP) as you all know, is a protocol developed by Microsoft that allows users to connect to other Windows operating systems with a graphical user interface (GUI). In order to enhance the RDP user experience and reduce the data throughput on your network, RDP Bitmap Cache was implemented. In layman's terms, what this essentially does, is store bitmap sized images of your RDP sessions into a file so that your session reuses these images and reduces the potential lag. Originally, this was designed when we thought dial-up Internet was legit and it was what we had to connect to other systems (side note: if you have not experienced Internet at dial-up speeds, you are 0xDEADBEEF 🥩 to me). The following image provides a screenshot of this option being set by default on Windows systems:
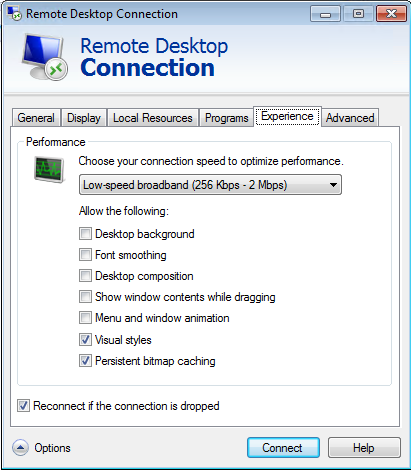
It is very important to note that these files are present only on the client system and not on the connecting host. This means that if an attacker connected to a compromised system via RDP from one of their own devices, you will not likely be able to collect this artifact. However, if an attacker decides to hop around your network, look at the source systems where the attacker is connecting from, and try to get these cache files.
I read this French bulletin by ANSSI/CERT-FR a while back and they provide a great breakdown of Bitmap Cache, but the problem is that it's in French and je ne parle pas français. But due to the beauty of the Internet, I was able to translate the whole bulletin, so, I will try my best to extract what was important from this writeup.
You can find these RDP Bitmap Cache files in two (2) different paths depending on your operating. If you are an archaic savage and still use Windows XP , they are located in the following path:
C:\Documents and Settings\<user_account>\Local Settings\Application Data\Microsoft\Terminal Server Client\Cache\*
However, for Windows 7 and above, they are located in the following location:
C:\Users\<user_account>\AppData\Local\Microsoft\Terminal Server Client\Cache\*
You can also change the path of where these files get cached if you wanted to, by playing around with the registry keys. Now, in terms of what you will see in these paths are two (2) different types of files. You have bcache##.bmc and Cache####.bin files. Note that the # represents a numeric value.
The "bcache" files are used for older versions of Windows and the max size that I have seen these files get to is 20MB. When I tested on a Windows 7 machine, these "bcache" files get created, along with the "Cache####.bin" files. These "bcache" files will either have the numbers 2, 22, or 24, and these numbers represent the quality of the bitmap images, in Bits Per Pixel (BPP), that are stored in their respective "bcache" files. Therefore, these files,represent the following bitmap image quality:
When attempting to render a bitmap image, the only difference is the quality and whether you can see things clearly.
On the other side, we have the "Cache####.bin" files are used for Windows 7 machines and above. The max size that these files get is up to 100MB, so once they reach the limit, Windows will start rolling out new files. They start at 0000 and increment from there (e.g. Cache0001.bin, Cache0002.bin, etc).
There aren't that many tools that can parse these files, but the ones that are out there, are outstanding. One of my favorite ones, and the one that is maintained the most, is "BMC Tools" by ANSSI/CERT-FR. Recently, in 2018, they added a feature that combines bitmap images together, thus stacking them one next to each other. Additionally, they parse both "bcache" and "Cache####.bin" files.
The other tool I recommend is "RDP Bitmap Cache Viewer", copyrighted to David Rees. However, this tool is no longer available and some copies can be found scattered across the world. Additionally, it only parses "bcache" files, so if you're looking to parse "Cache####.bin" files, you are out of luck. However, for this blog post, I will show you this tool, as I have collected sample "bcache" files.
Finally, you can write up a parser yourself in Python, Golang, or PowerShell.
I ran a couple of tests in my own personal lab pretending to gain access to a system via RDP. In my case, an attacker known as "T3rr1be H4ck3r" (who apparently also has terrible spelling 🤦🏻♂️) got access to a Windows 7 workstation, and then later jumped onto a Windows Server 2008 to dump credentials using Mimikatz. The following images represent actual screenshots of the attack, so please note that this is not the results from the Bitmap Cache files.
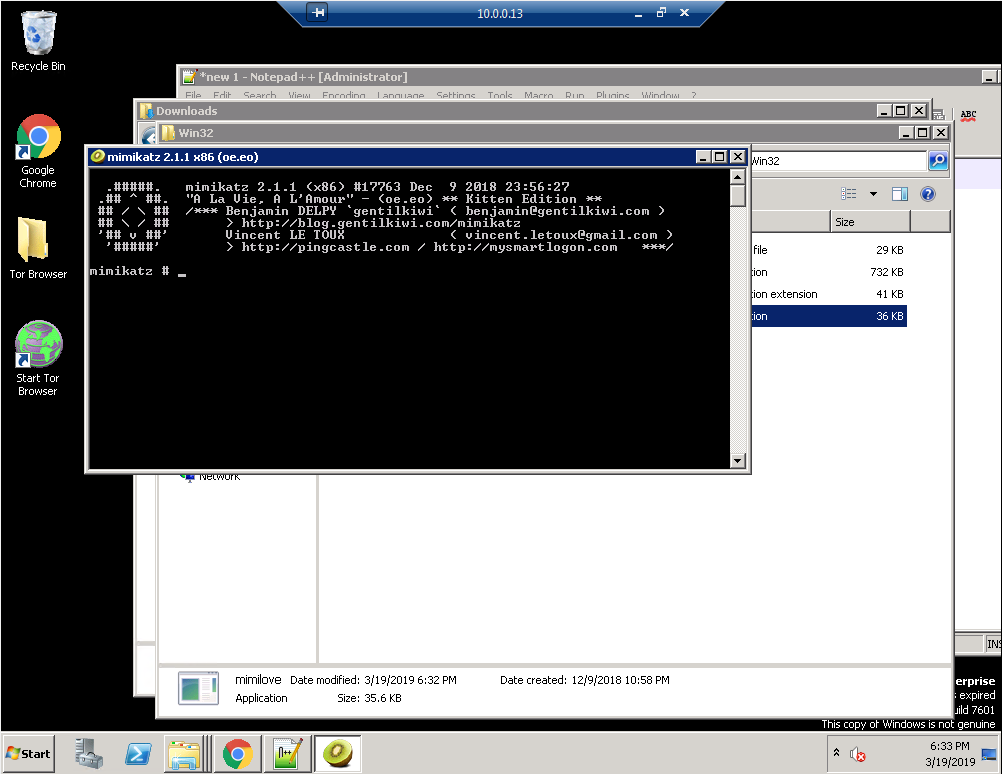
Now, after this incident occurred, I accessed the compromised Windows 7 workstation and collected the "bcache22.bmc" file that was present. As I mentioned before, for this "demo" I used the "RDP Bitmap Cache Viewer" tool. It is as simple as running the tool, selecting the "bcache" file, and the BPP settings. Given that it's a "bcache22.bmc" file, we know that we need to configure the settings to 16 BPP. The following figure provides a screenshot of the tool with the loaded "bcache" file:
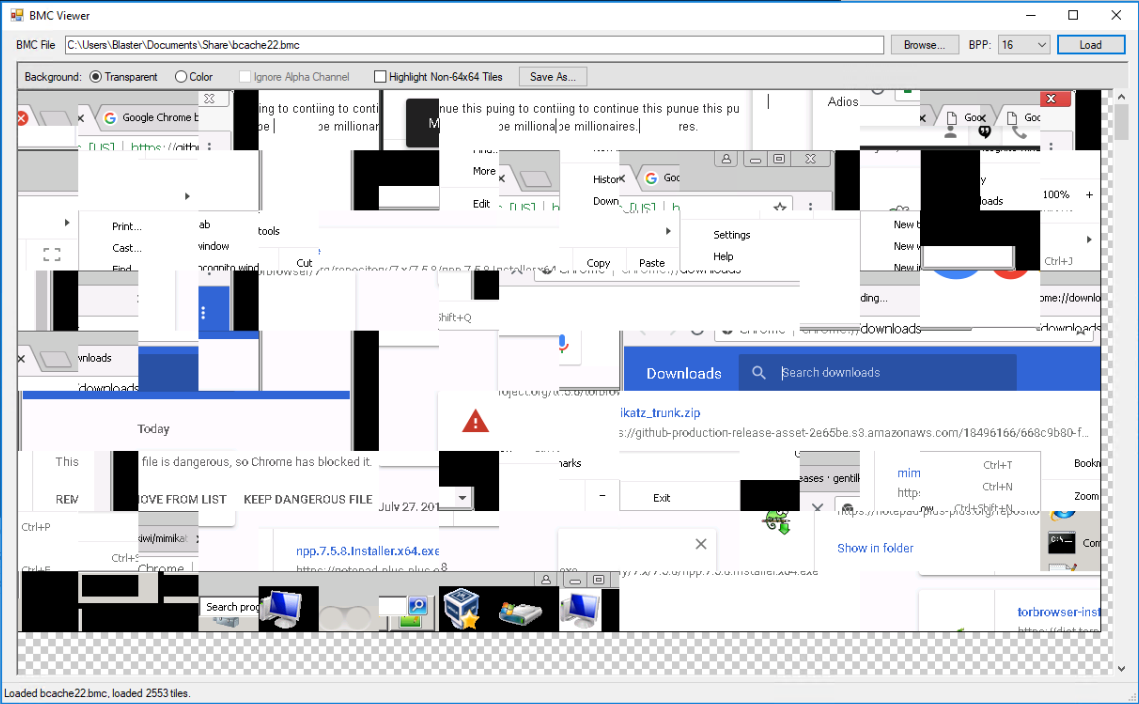
As you can see, these are all of the bitmap cache images stacked next to each other. The simplistic beauty of this tool, is being able to resize the window. By doing so, you can shift the images according to when it was created (i.e. top-left is old, bottom-right is recent) and combining different bitmap images that could potentially be related to one another (e.g. Look at Google Chrome's "Download" bar in a sequence of bitmap images).
Now if we take a closer look into this "bcache" file, we can tell that the attacker has done a couple of things on the server:
If you want, you can open up the images below in a new tab to take a closer look at what I was able to spot, as I have circled important items in red.
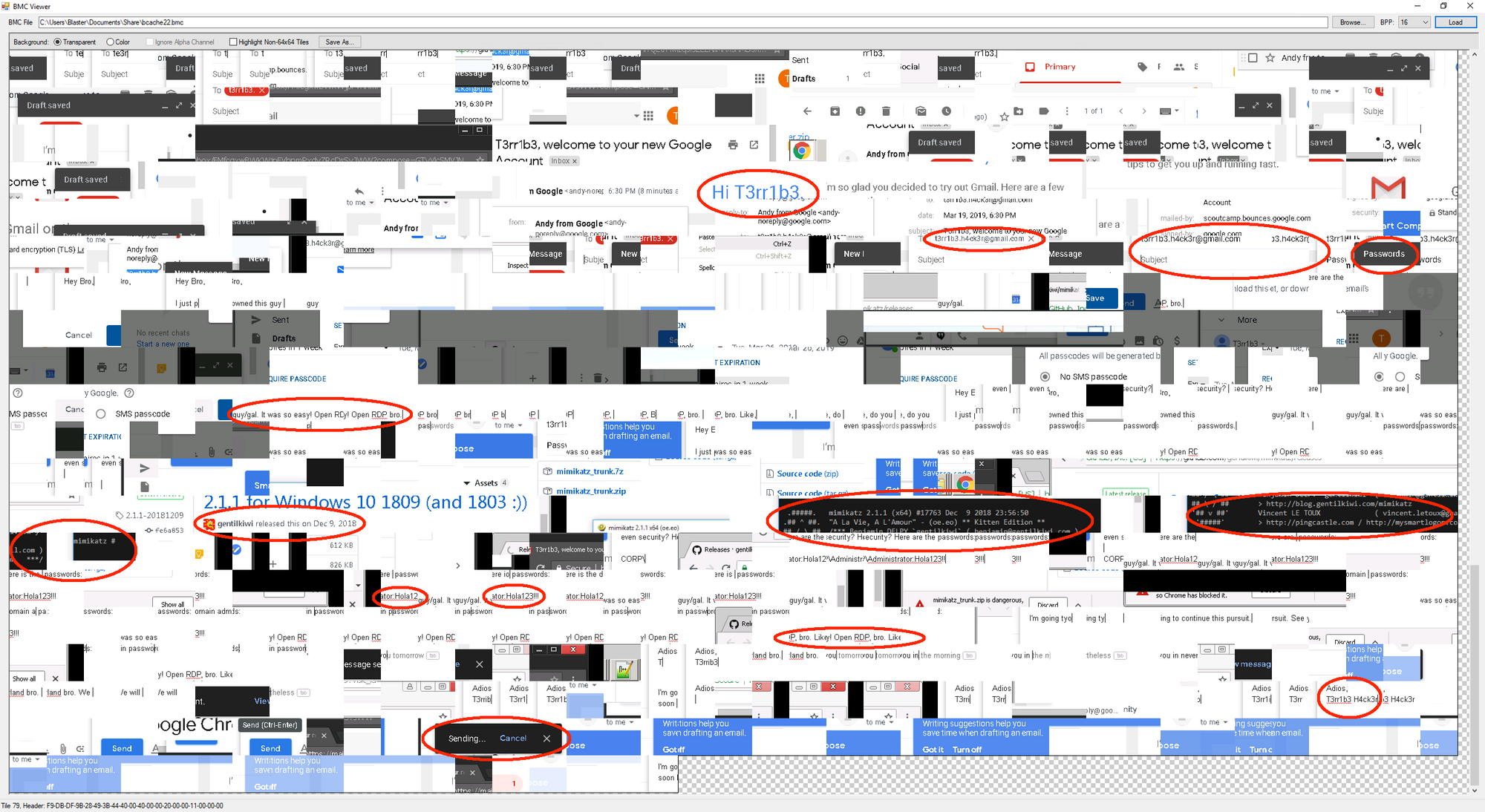

Again, it's important to note that the bitmap images at the top usually indicates the oldest bitmaps recorded in this file, and that the bottom ones are the most recent ones. Therefore, if we take into account the creation of the file and the timeframes the attacker authenticated onto the server (i.e. look at the Terminal Services logs), we can come up with a story of what happened and attempt to depict it visually.
There's definitely a lot that we can grasp from these RDP Bitmap Cache images. It most certainly can give you a timeline of events that occurred in an RDP session. Granted, this is assuming that the threat actor was the only one authenticating to the server, but then again, even if multiple users, legitimate and illegitimate ones, used that workstation to authenticate to different servers, we can at least tell if malware was potentially executed (e.g. Mimikatz terminal, malicious filenames, etc). If these bitmap images were cached, at least it could also help you tell if there has been further exposure across your network.
Personally, I use this as a great marketing campaign for an investigation; get to show the other side of the table, where we can "closely" see what the attacker is viewing from his/her perspective. I hope that this blog post has shed some light on what RDP Bitmap Cache is and how you can leverage it in your investigation, and hopefully you can troll threat actors to "cache you outside" (I know, lame joke).